Hackers are actively hitting more than 1.6 million WordPress sites in coordinated large-scale attack campaigns originating from 16,000 IP addresses. They are doing this by exploiting security bugs in four WordPress plugins and 15 Epsilon Framework themes.
WordPress security company Wordfence, said Thursday it had detected and blocked more than 13.7 million attacks aimed at the plugins and themes in a period of 36 hours. The exploits make it possible for attackers to update arbitrary options on vulnerable websites resulting in the taking over the breached websites and carrying out further malicious actions.
Attackers are targeting 4 individual plugins with Unauthenticated Arbitrary Options Update Vulnerabilities. The four WordPress plugins in question are:
- Kiwi Social Share <= 2.3 – patched on November 12, 2018,
- Pinterest Automatic <= 4.14.3 – patched on August 23, 2021
- PublishPress <= 3.53.2 – patched on December 6, 2021
- WordPress Automatic <= 2.0.10 – patched on August 23, 2021
The following is the list of affected Epsilon Framework theme versions:
- Activello <=1.4.1
- Affluent <1.1.0
- Allegiant <=1.2.5
- Antreas <=1.0.6
- Bonkers <=1.0.5
- Brilliance <=1.2.9
- Illdy <=2.1.6
- MedZone Lite <=1.2.5
- NatureMag Lite – (No known patch yet)
- NewsMag <=2.4.1
- Newspaper X <=1.3.1
- Pixova Lite <=2.0.6
- Regina Lite <=2.0.5
- Shapely <=1.2.8
- Transcend <=1.1.9
How do I know if my WordPress Site has Been Hacked?
The exploit on over 1.6 million WordPress sites involves hackers updating the users_can_register option to ‘enabled‘ and set the default_role option to ‘administrator‘.
The simplest way to check if your site has been compromised by exploiting these vulnerabilities, you should review the user accounts on the site to determine if there are any unauthorized user accounts. Secondly, check if the site is running a vulnerable version of any of the four plugins or various themes mentioned earlier in this post.
If you have a combination of the above scenarios then it is highly likely that you have been compromised.
You need to fix the problem immediately by removing any detected rogue user accounts immediately and updating the affected plugins and themes.
If you are using the NatureMag Lite theme then you need to uninstall it and replace it with an alternative.
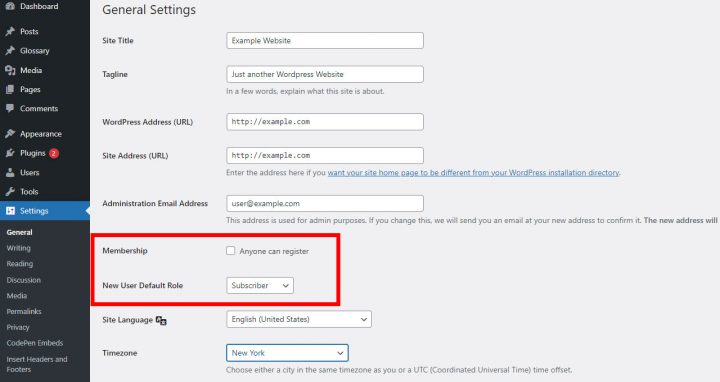
Finally, review the settings of the site and ensure that they have been set back to their original state. You can find these settings by going to your WordPress site and navigating to the equivalent page to http://example.com/wp-admin/options-general.php.
Please make sure the ‘Membership‘ setting is correctly set to what you intended it to be. Next, check that the ‘New User Default Role’ is set to the appropriately expected value. If it is ‘Administrator‘ we strongly recommend not using it for the new user default role as this can lead to serious consequences when the site is compromised.
In Summary
Share this post within the WordPress community to create awareness among site owners about this distributed attack campaign and how to defend against it.
To recap, this post highlights how attackers are actively attempting to exploit over 1.6 million WordPress sites targeting various plugins and themes that make it possible for attackers to effectively take over the vulnerable sites through the use of arbitrary option updating. It is good practice to ensure that your sites are fully updated to the patched versions of the plugins and themes.
Found this article interesting? Follow Brightwhiz on Facebook, Twitter, and YouTube to read and watch more content we post.